The File Transfer Protocol or FTP is a protocol used to access files on servers from private computer networks or the Internet. vsftpd, (or very secure FTP daemon) is an FTP server for Unix-like systems, including Linux. It is licensed under the GNU General Public License. It supports IPv6 and SSL. vsftpd is the default FTP server in the Ubuntu, CentOS, Fedora, NimbleX, Slackware and RHEL Linux distributions.
Warning – FTP data transfer is inherently insecure; traffic is not encrypted, and all transmissions are done in clear text (including usernames, passwords, commands, and data). Consider securing your FTP connection with SSL/TLS.
This blog shows you how to install and configure the Very Secure FTP Daemon (vsftpd) on CentOS 7 and how to authenticate with Windows Active Directory.
Install & Configure VSFTPD Daemon
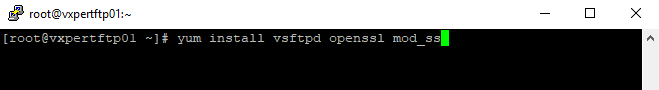
Install vsftpd and openssl packages on the Centos 7 Linux server
# yum install vsftpd openssl mod_ss
FTP data is usually insecure since information (usernames, passwords, commands, data) is transmitted unencrypted in clear text. Therefore, it’s very IMPORTANT to encrypt the FTP connection using SSL/TLS. Generate a self-signed certificate to secure the FTP server connections.
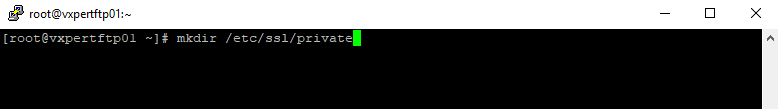
Create a directory to save the SSL key or you can save default VSFTPD location.
#mkdir /etc/ssl/private
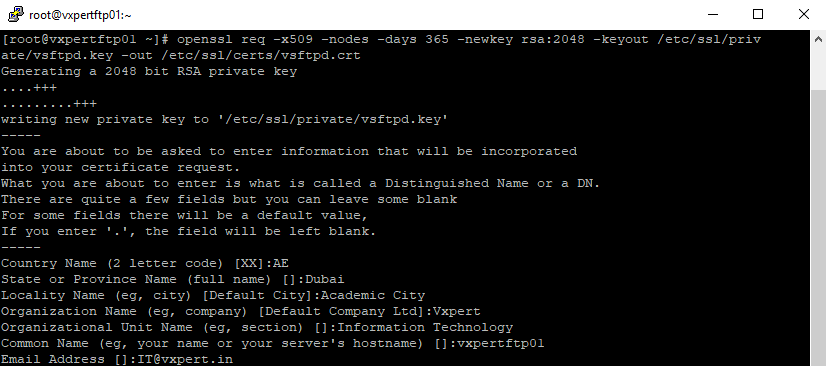
Generate a self-signed certificate to secure the FTP server connections.
#openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /etc/ssl/private/vsftpd.key -out /etc/ssl/certs/vsftpd.crt
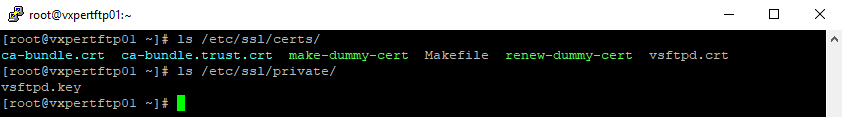
Make sure the Certificate and Private Key is created on the locations
Edit the configuration file /etc/vsftpd/vsftpd.conf
#vi /etc/vsftpd/vsftpd.conf
Disallow anonymous logins; this allows unidentified users to access files via FTP. Ensure that the anonymous_enable setting to NO:
anonymous_enable=NO
Enable local users to login, this will allow your regular user accounts to function as FTP accounts. Change the local_enable setting to YES:
local_enable=YES
If you want local user to be able to write to a directory, then change the write_enable setting to YES:
write_enable=YES
Local users will be ‘chroot jailed’ and they will be denied access to any other part of the server. Set the chroot_local_user setting to YES:
chroot_local_user=YES

Add the below lines to enable SSL/TLS on VSFTPD
This option enables our SSL support for vsftpd.
ssl_enable=yes
Prevent anonymous SSL/TLS encrypted login, in essence, the guest user.
allow_anon_ssl=NO
We’re going to force SSL/TLS encryption of both your username/password and your data to keep it safe.
force_local_data_ssl=YES force_local_logins_ssl=YES
Use the stronger, better, encryption offered by TLS 1.1 and 1.2.
ssl_tlsv1_1=YES ssl_tlsv1_2=YES
TLS 1.0 is getting a little more insecure than we would like, so we are going to disable it. Please note that some older FTP clients are not compatible with newer TLS versions and may require this option to be set to “YES”.
ssl_tlsv1=NO
To keep the FTP connections safe against the BEAST and POODLE vulnerabilities we are going to disable SSLv2 and SSLv3.
ssl_sslv2=NO ssl_sslv3=NO
Continuing our security improvements, we are going to add some additional protection against Man in The Middle (MITM) attacks by enabling the following. This may not be compatible with some older FTP clients. If you experience connection loss try setting this option to “NO”.
require_ssl_reuse=YES
This will require the server to use stronger cipher suites.
ssl_ciphers=HIGH
Lastly, our created crt and key file.
rsa_cert_file=/etc/ssl/certs/vsftpd.crt rsa_private_key_file=/etc/ssl/private/vsftpd.key
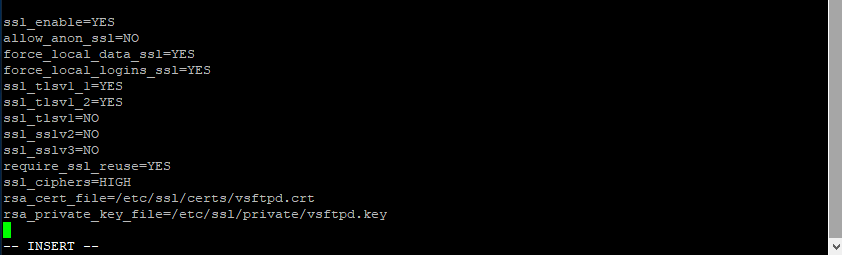
To exit type “: wq” and that will save the file and quit the program.
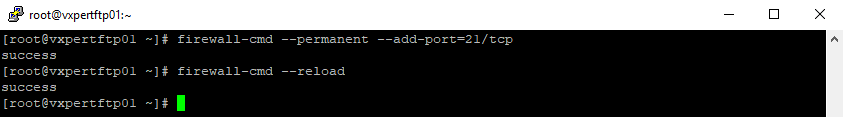
Allow the default FTP port, port 21, through firewalld, and reload the firewall
#firewall-cmd --permanent --add-port=21/tcp #firewall-cmd –reload
Special Note: Vsftpd also uses ssh port i.e. 22 so ensure firewall-cmd allows for ssh connections
Then set the vsftpd service to start at boot:
#systemctl enable vsftpd
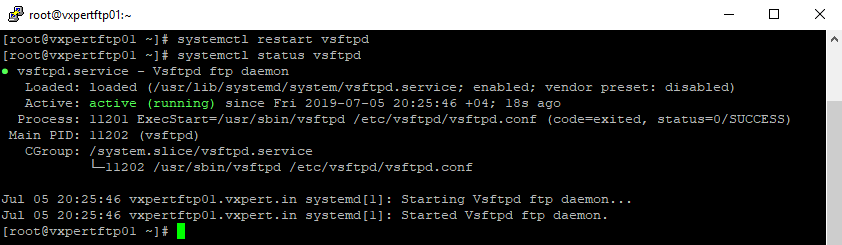
Now restart and check the status of VSFTPD
#systemctl restart vsftpd #systemctl status vsftpd
Now create a local user to test the FTP access
#useradd ftpuser #passwd ftpuser
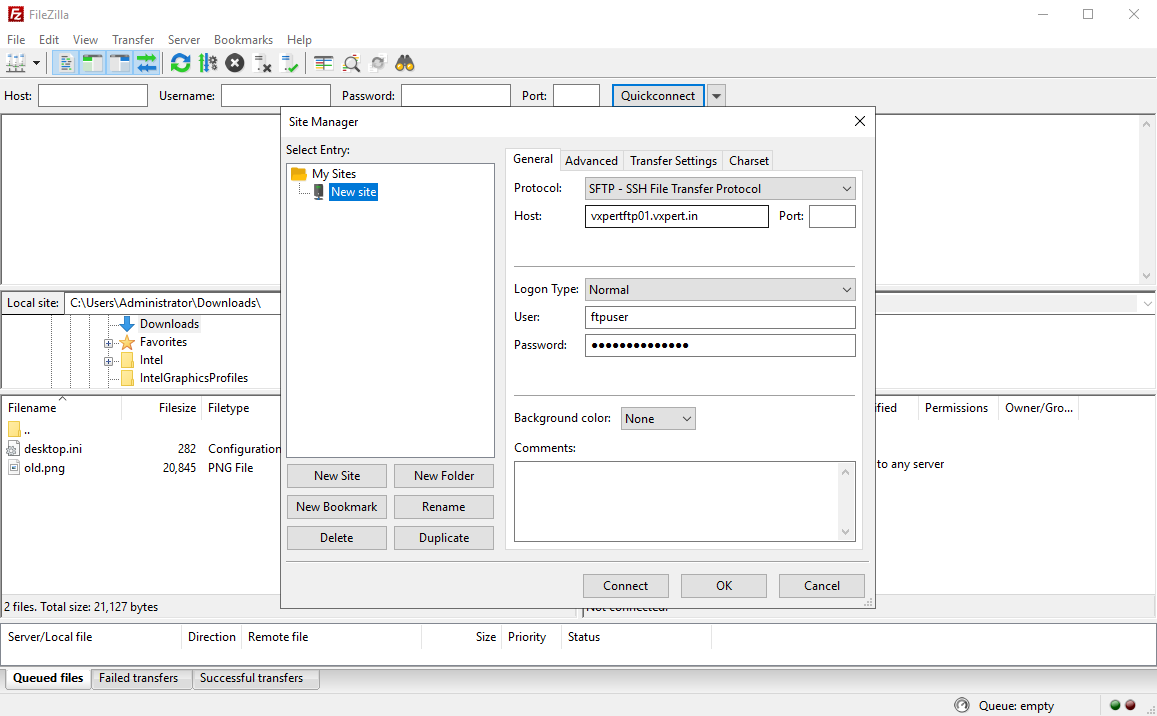
Now that we completed all configuration and daemon is started, we should be able to start uploading/downloading.
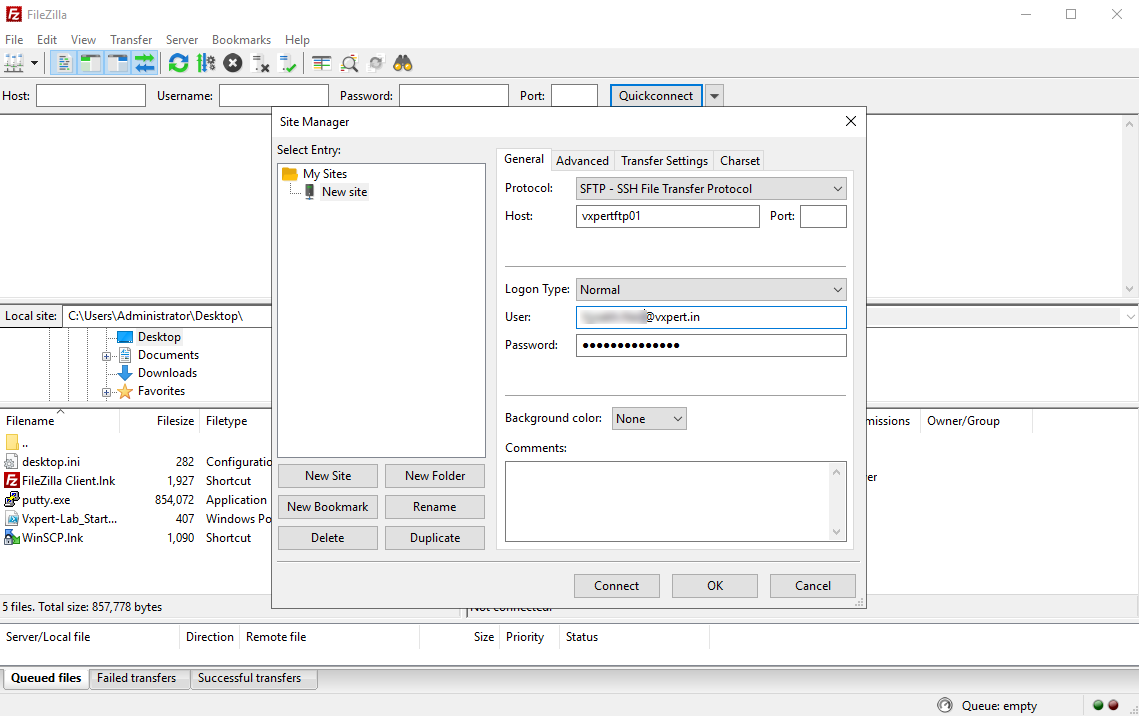
I am using FileZilla to connect VSFTD like below, Open Site Manger to configure your FTP connection
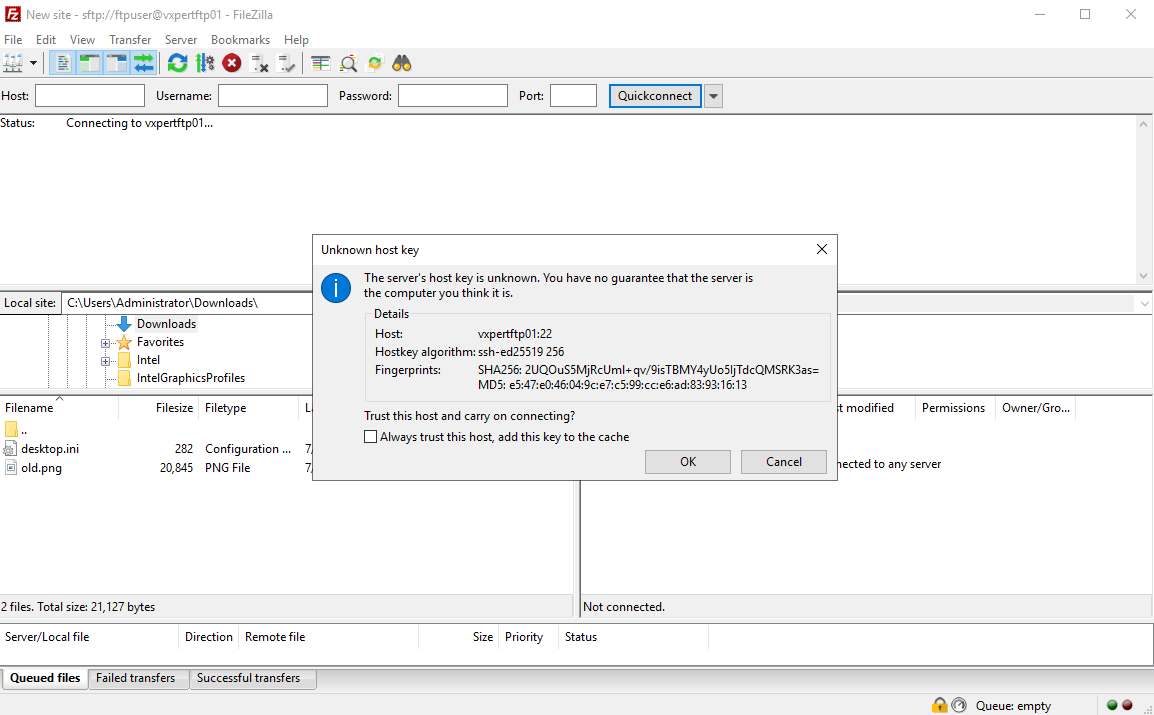
when you connect will get a pop-up to trust the certificate which we created. Click OK to connect
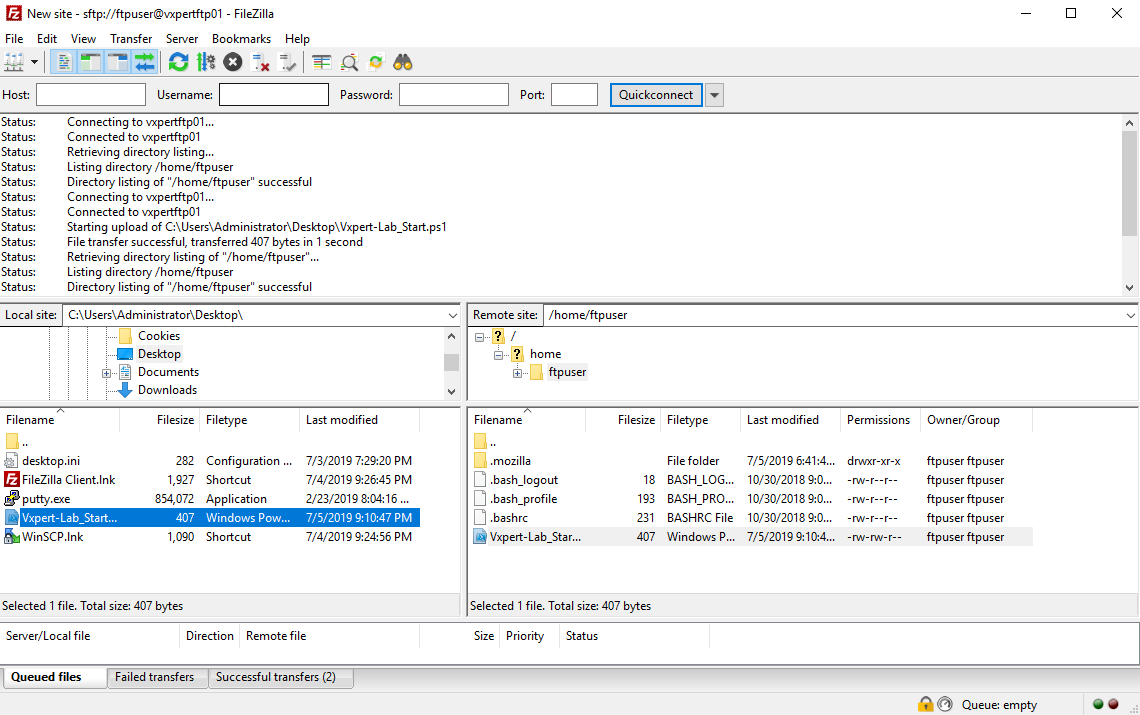
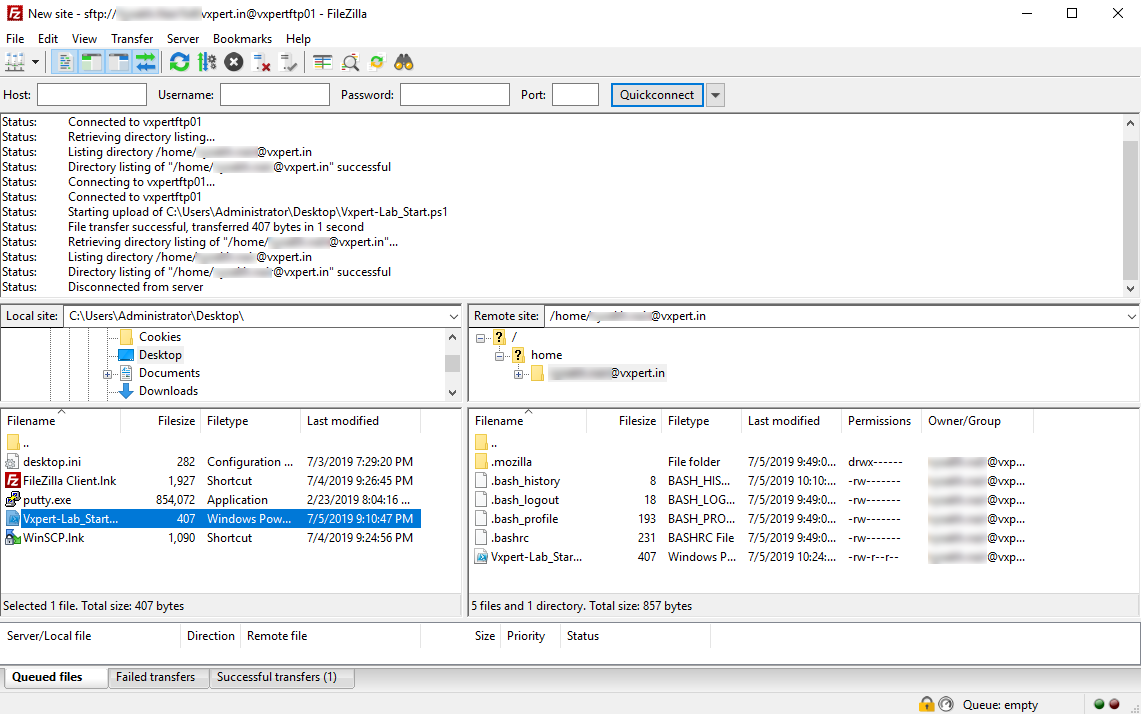
I can connect successfully and upload file to my FTP server.
Configure Active Directory Authentication
In Most of the Organizations users and groups are created and managed on Windows Active Directory. We can integrate our CentOS 7 servers with Active Directory for SSH/VSFTPD authentication purpose. In other words, we can join our CentOS 7 Server on Windows Domain so that system admins can login to these Linux servers with Active Directory credentials. While creating UNIX users on AD we can map these users to a specific group so that level of access is controlled centrally from AD.
Use the yum command to install following packages from the command line.
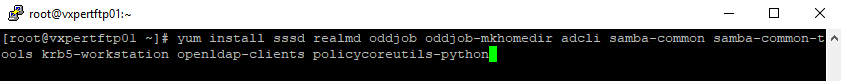
#yum install sssd realmd oddjob oddjob-mkhomedir adcli samba-common samba-common-tools krb5-workstation openldap-clients policycoreutils-python
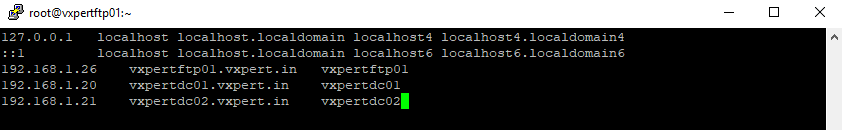
Update the /etc/hosts file and /etc/resolv.conf so that dns name or hostname of AD server gets resolved correctly.
#vi /etc/hosts
#vi /etc/resolv.conf

Use below command to Join this server to Domain, the username should have enough privileges to join a server to domain.
#realm join --user=username vxpert.in
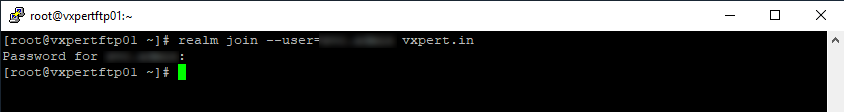
Now verify whether our server has joined the Windows domain or not. Simply run below command
#realm list
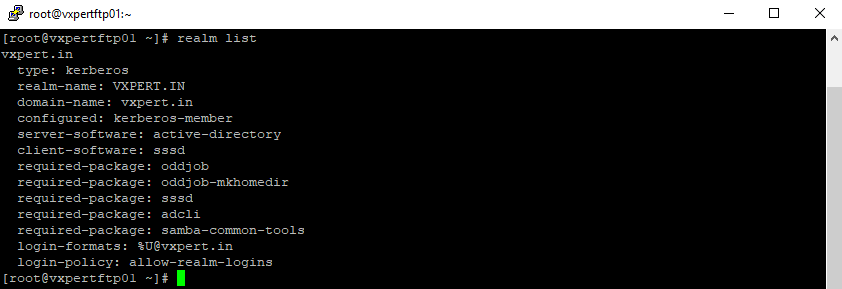
Whenever we run ‘realm join’ command it will automatically configure ‘/etc/sssd/sssd.conf‘file.
With ‘id‘command on Linux we can verify the user’s uid and gid and their group information. At this point of time our server is now the part of windows domain. Use below command to verify AD users’ details
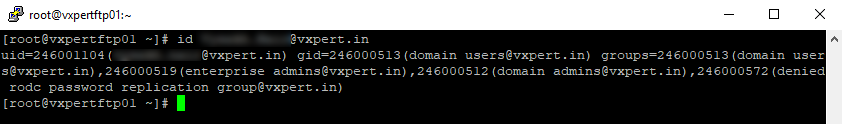
Now all users in Active Directory can login to this Server, which not a secured way. Now will restrict login access to specific Active Directory Group.
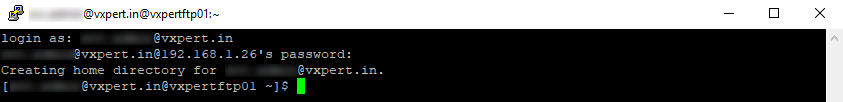
I have created an Active Directory Group name LinuxAdmin, we will allow access to only this group members and restrict all other. Open the sssd configuration file
#/etc/sssd/sssd.conf

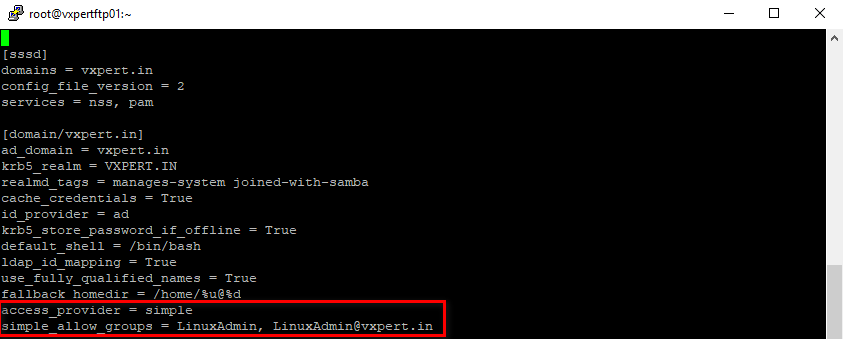
Add the below highlighted lines
access provider = simple simple_allow_groups = LinuxAdmin
Or you can enter below command which will automatically update configuration file
#realm permit -g [email protected]
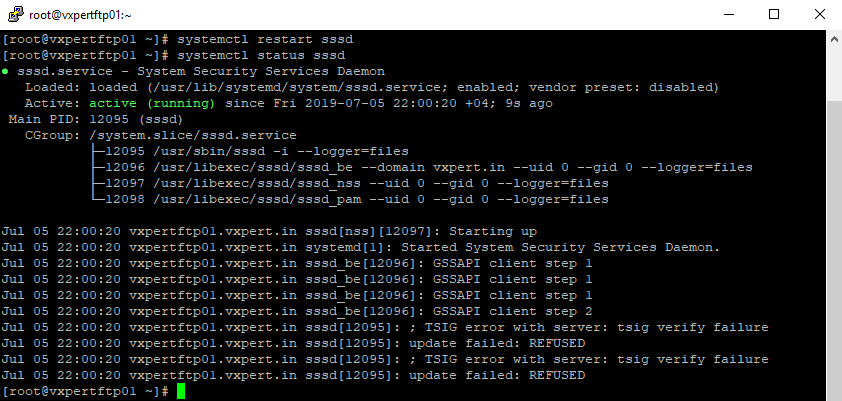
Restart the service and check the status
#systemctl restart sssd #systemctl status sssd
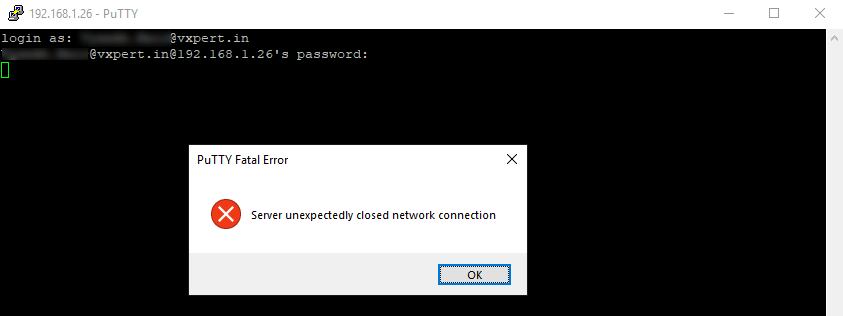
When you try to login with Domain account you won’t be able to login as you are not a member of that group.
Try to access after adding your username to LinuxAdmin group.
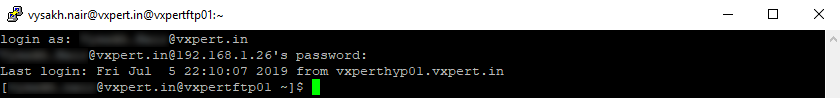
I can successfully login to the SSH session, Our Active Directory authentication is working well.
In case you want to configure sudo rights for AD users/group then the best way is to create a group on AD and add Linux/UNIX users in that group and on Linux Server create a file under the folder /etc/sudoers.d/
#vi /etc/sudoers.d/LinuxAdmin

Put the following content in the file, in my case I have given all the rights to the users which are part of LinuxAdmin group.
%[email protected] ALL=(ALL) ALL
Now connect your FTP also using FileZilla client, only LinuxAdmin members can access the FTP as well.
That’s all from this blog, hope you guys got an idea about how to install and configure vsftpd on Linux and how to join CentOS server with Windows Domain and authenticate SSH/VSFTPD with domain account with group restriction.
Thanks,
If you have any comments, please drop me a line.
I hope this article was informative, and don’t forget to buy me a coffee if you found this worth reading.



Leave a Reply