The NSX Distributed Firewall implements a stateful packet filtering capability on each vNIC of every virtual machine (VM) under its management. In addition to the control of traffic arriving at the VM from outside the network to which the VM is connected, the Distributed Firewall allows control of traffic between VMs on the same network. This granular control of traffic within the same network is known as micro-segmentation. Micro-segmentation allows a degree of control over traffic that has already been allowed through the perimeter firewall which has not, previously, been possible.
As we are talking the Distributed Firewalling in the context of VMware Cloud Director, we must talk discuss about the Data Center Groups. In this blog we will talk on how to create Data Center Group and configure Distributed Firewalling in VMware Cloud Director Provider Virtual Data Center which is backed by NSX-T.
Data Center Group
A data center group acts as a cross-VDC router that provides centralized networking administration, egress point configuration, and east-west traffic between all networks within the group. A data center group can contain between one and 16 VDCs that you configure to share an active egress point. Also, you can only enable Distributed Firewalling only under a Data Center Group
Configure Data Center Group
Before creating a Data Center Group Provider must create a Compute Provider Scope, which is just a abstraction of Fault Domain or Availability Zone and is done at either Provider VDC level or vCenter level.
To Configure Compute Provider Scope, Click on Infrastructure Resources and EDIT the vCenter Server Settings and update vale as shown below figure.
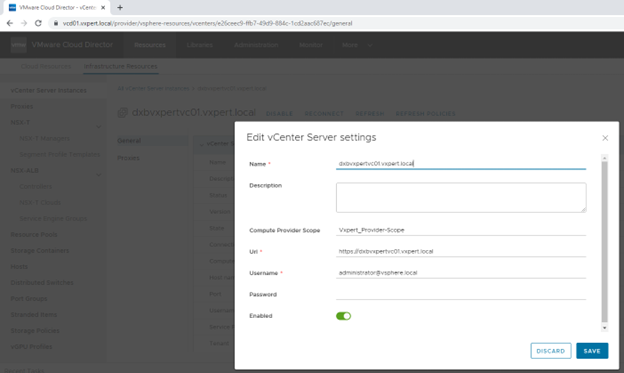
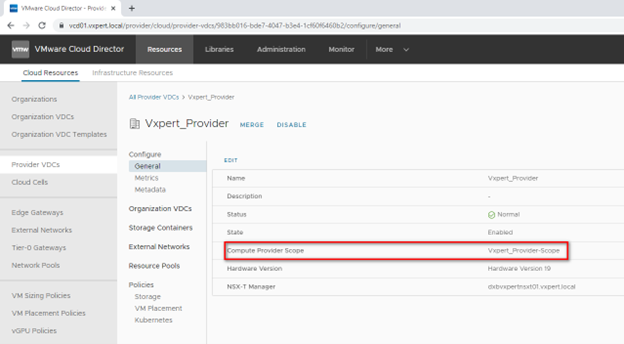
After that Provider vDC backed by same vCenter will be automatically updated by this Provider Scope value. Click on Provider vDC – General.
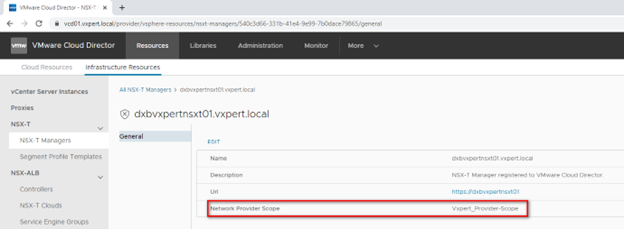
The Same can be configured in NSX-T manager where you want to define the Network Provider Scope
To Configure Network Provider Scope, Click on Infrastructure Resources and EDIT the NSX-T Managers Settings and update vale as shown below figure.
Now the provider can create Data Center Group for tenants.
Create Data Center Group
To create a Data Center Groups, switch to tenant console and click on Networking – Data Center Groups
Click on NEW to create the Group and select the Starting vDC and click Next
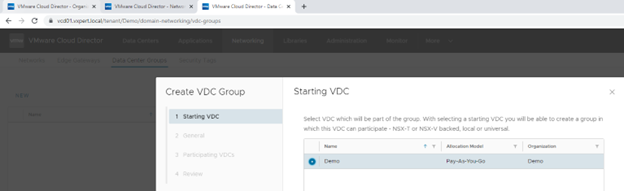
Provide the Data Center Group name and click Next
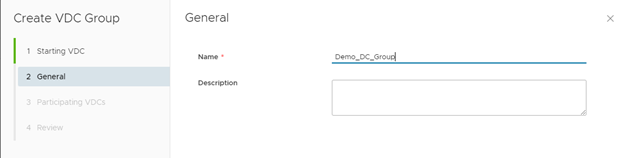
Select the Participating vDC and Click Next
Note: – Here you can group of 1 -16 Organization Virtual Datacenters. As I don’t have any other VDC part of same Organization I am selecting the same organization as our intention is to only enable Distributed Firewalling between networks in same organization. You can also enable other vDC which is part of same Organization to share the network between them.
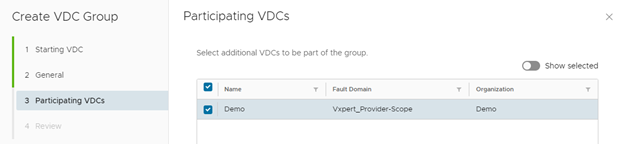
Review the configuration and click on Finish
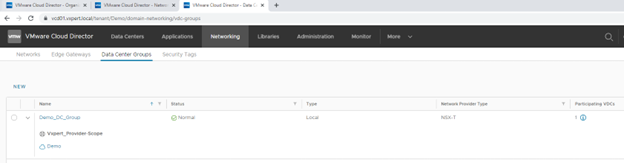
Assign and Edge Gateway to Data Center Group
To assign Edge Gateway to a Data Center Group Click on Data Center Group and select Edge Gateway and click on Add Edge
Note: – Adding an Edge to a VDC Group will simply increase the scope of an Edge from a VDC Edge to a VDC Group Edge. The promotion process does not change the underlying services or networks. This simply makes the Edge Gateway available in all associated VDC workloads to connect to routed networks.
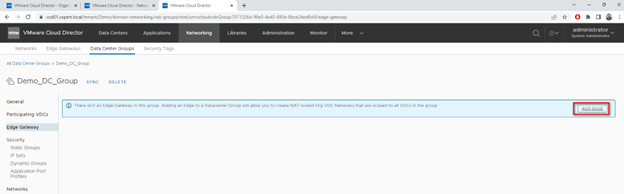
Select the Edge Gateway and click on SAVE
Note: – only one Org VDC Edge Gateway can be added to the Data Center Group. This is due to the limitation that NSX-T logical segment can be attached and routed only via single Tier-1 GW. The Tier-1 GW is in active / standby mode and can theoretically span multiple sites, but only single instance is active at a time (no multi-egress).
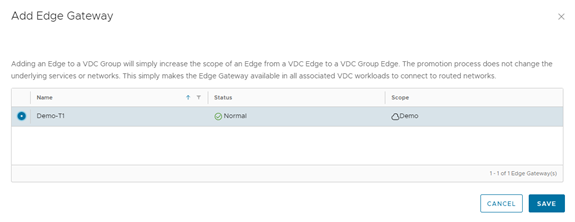
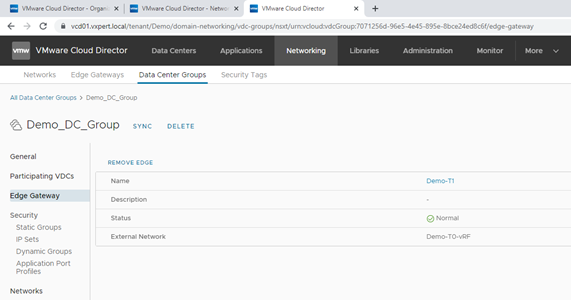
Routed networks will automatically be added to a Data Center Group if they are connected to the group Org VDC Edge Gateway. Isolated networks must be added explicitly.
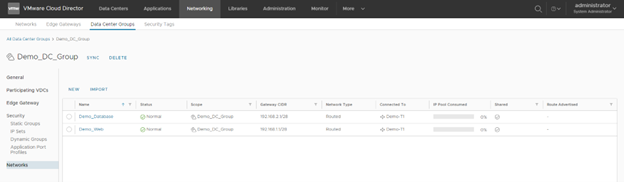
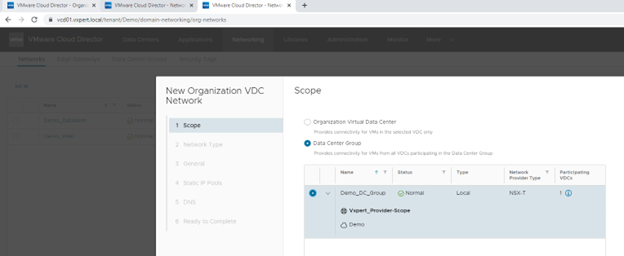
To add a new network which you need to share across the organization vDC you can add Net Network under Data Center Group like below figure. The Organization network will be visible across the participating Virtual Data Centers in the Group.
Activate Distributed Firewalling
To enable the tenant to use DFW, it must be explicitly enabled, and the tenant Organization must have the correct rights, the “write” permission to “Configure VDC Group” must be added by the provider to the “Default Rights Bundle” or assigned to a new one. Only after the modified rights bundle is published to tenants, the feature will be available to an Org Admin.
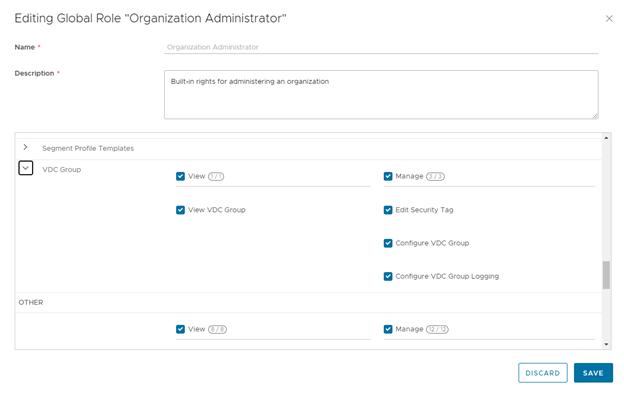
To enable the Distributed Firewall provider should Activate it under the Data Center Group
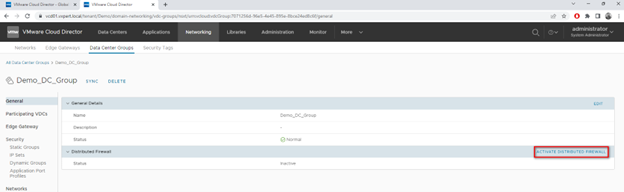
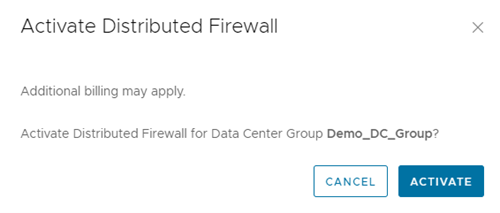
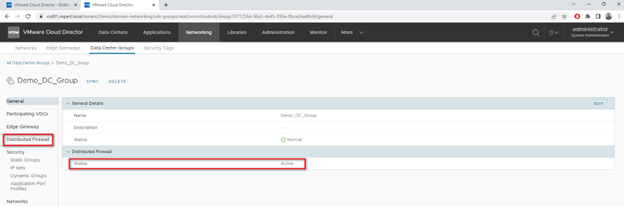
Once enabled you can see the Distributed Firewall Status is Active and a seprate tab got added for Fireall rules.
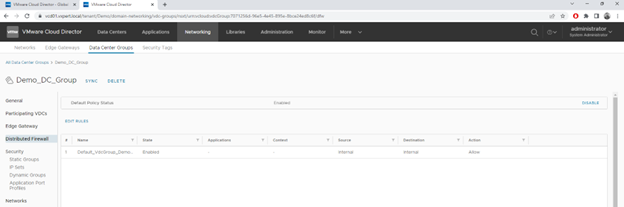
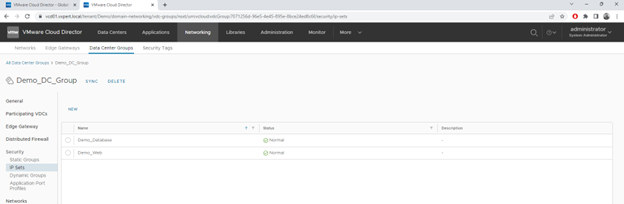
The DFW supports below groupings of objects to configure the firewall rules. You can create these grouping depends on your requirement and add this the firewall rules.
Static Groups
Dynamic Group (Security Tags/VM names)
IP Sets
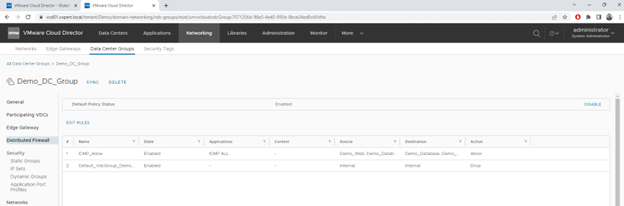
As you can see in below image, I have changed the default policy from Allow to Drop and added a new policy on top of that to allow ICMP packets between the Web and Database subnets which is part of Data Center Group using IP Sets
Thanks,
If you have any comments, please drop me a line.
I hope this article was informative, and don’t forget to buy me a coffee if you found this worth reading.



Leave a Reply