VMware NSX is the network virtualization platform that enables the implementation of virtual networks on your physical network and within your virtual server infrastructure. VMware NSX Data Center delivers virtualized networking and security entirely in software, completing a key pillar of the Software-defined Data Center (SDDC), and enabling the virtual cloud network to connect and protect across data centers, clouds, and applications.
NSX reproduces the entire network model in software, enabling any network topology—from simple to complex multi-tier networks—to be created and provisioned in seconds. It enables a library of logical networking elements and services, such as logical switches, routers, firewalls, load balancers, VPN, and workload security. Users can create isolated virtual networks through custom combinations of these capabilities.
Components
NSX consist of multiple components which can be categorized under different planes
- Data
Plane
- Logical Switches
- Distributed Logical Router (DLR)
- Distributed Firewall
- NSX Edge – Firewall, Load Balancer, IPSEC, L2 and SSL VPN
- Control
Plane
- DLR Control VM
- NSX Controller
- Management
Plane
- vCenter
- NSX Manager – Always has a 1-to-1 relationship with vCenter Server
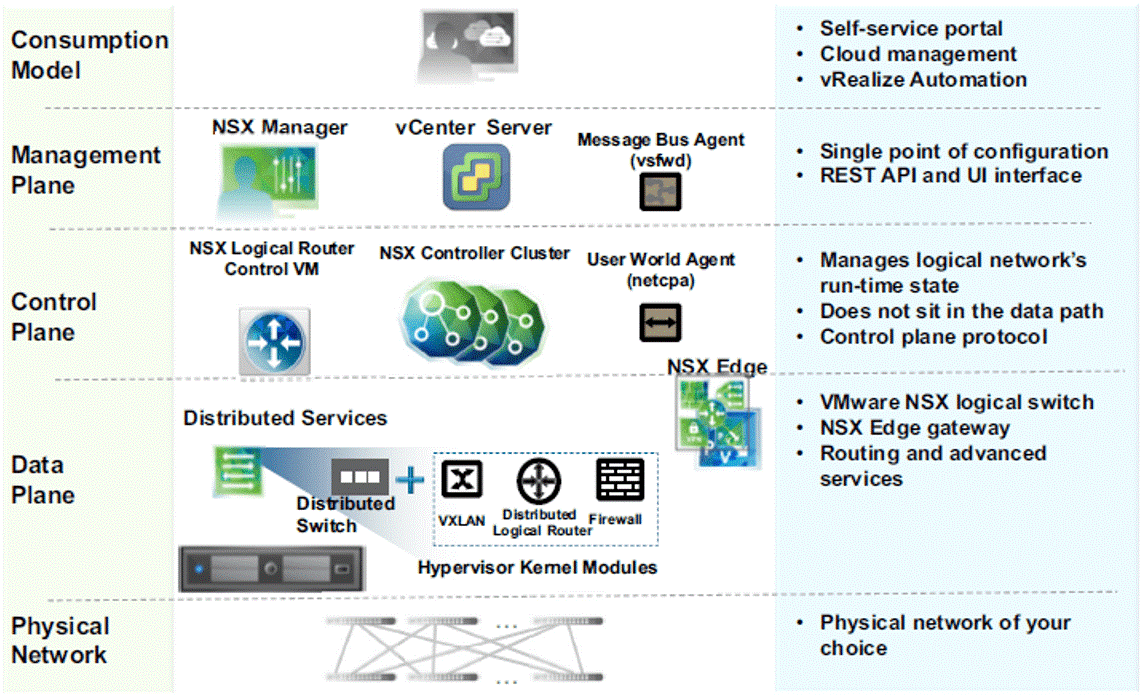
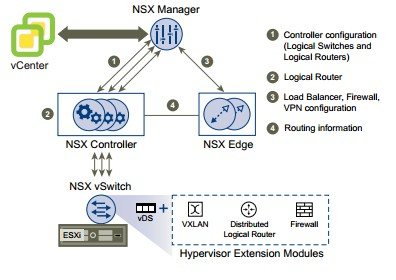
Below I am explaining the important functional components of NSX
NSX vSwitch
In an NSX domain, NSX vSwitch is the software that operates in server hypervisors to form a software abstraction layer between servers and the physical network. NSX vSwitch is based on vSphere distributed switches (VDSs), which provide uplinks for host connectivity to the top-of-rack (ToR) physical switches. The NSX virtual switch includes additional functionality from the traditional virtual switch. The key feature is the ability to use VXLAN to span layer 2 segments between hosts without the use of multiple stretched VLAN’s.
VMware NSX Manager
VMware NSX Manager is a virtual appliance which provides integration with VMware vCenter Server which allows you to manage the VMware NSX environment through VMware vCenter. All VMware NSX operations and configuration are done through VMware vCenter, which communicates with VMware NSX Manager through APIs to delegate tasks to the responsible owner.
VMware NSX Controller
NSX controller is a virtual appliance which is deployed by NSX Manager. All virtual network provisioning and MAC address learning is handled through the VMware NSX Controller. You can think of the VMware NSX Controller as the virtualized control plane of the SDN network. It provides a control plane to distribute network information to hosts. To achieve a high level of resiliency the NSX Controller is clustered for scale out and HA.
NSX controller cluster provides intelligence and features to Logical switches. NSX controller eliminates the need for Multicast configuration in physical network and it reduces the broadcast traffic by suppressing ARP requests.
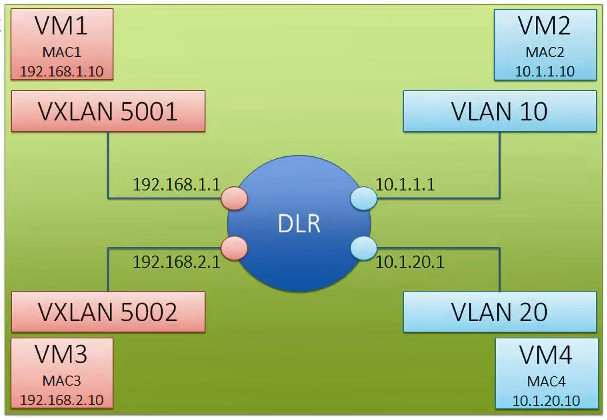
VMware NSX Distributed Logical Router
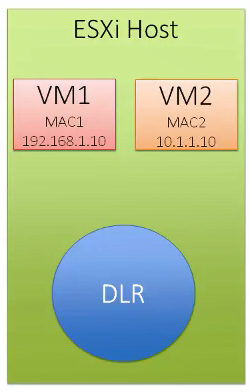
NSX Distributed Logical Router provides an optimized distributed hypervisor level routing functionality for East-West traffic within the data center and there-by preventing hair-pinning scenarios. DLR consist of DLR kernel modules, which get installed on hypervisor and DLR control VM, which is a virtual appliance and the role is to peer with NSX Edges. NSX DLR has below functionalities.
- Default gateway for all VMs
- MAC address learning and flooding
- Bridging and routing all packets between different virtual networks
- Peers with the VMware NSX Edge to progress egress traffic outside of the virtual networks
- Virtual tunnel endpoint (VTEP) termination
- Security policies and enforcement
- Multi-tenancy
VMware NSX Edge Gateway
NSX Edge is a virtual appliance deployed from NSX Manager. The VMware NSX Edge Gateway is responsible for bridging the virtual networks with the outside world. It acts as a virtual WAN router that can peer with physical networking equipment so that all the internal virtual networks can access the Internet, WAN, or any other physical resources in the network. The VMware NSX Edge Gateway can also provide centralized security policy enforcement between the physical network and the virtualized networks.
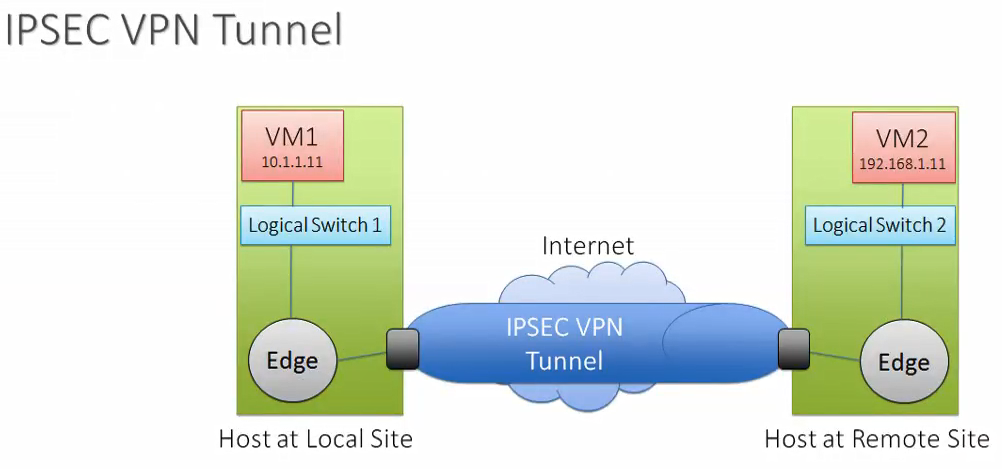
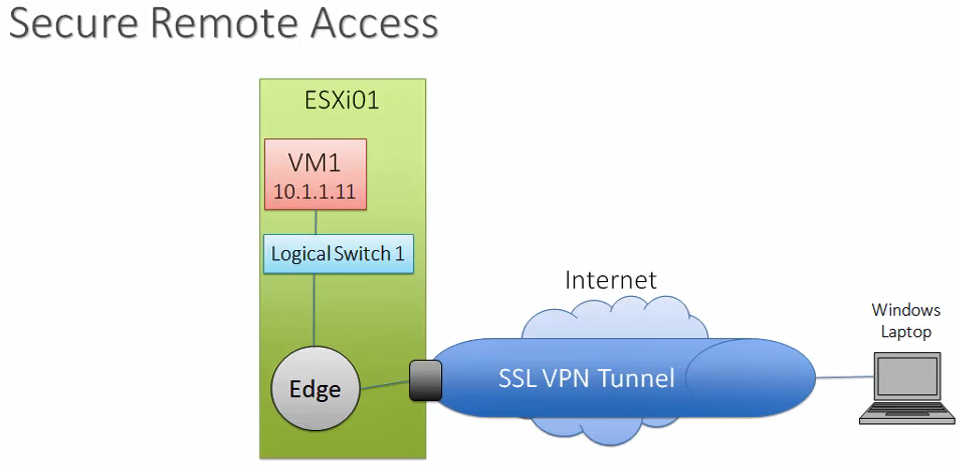
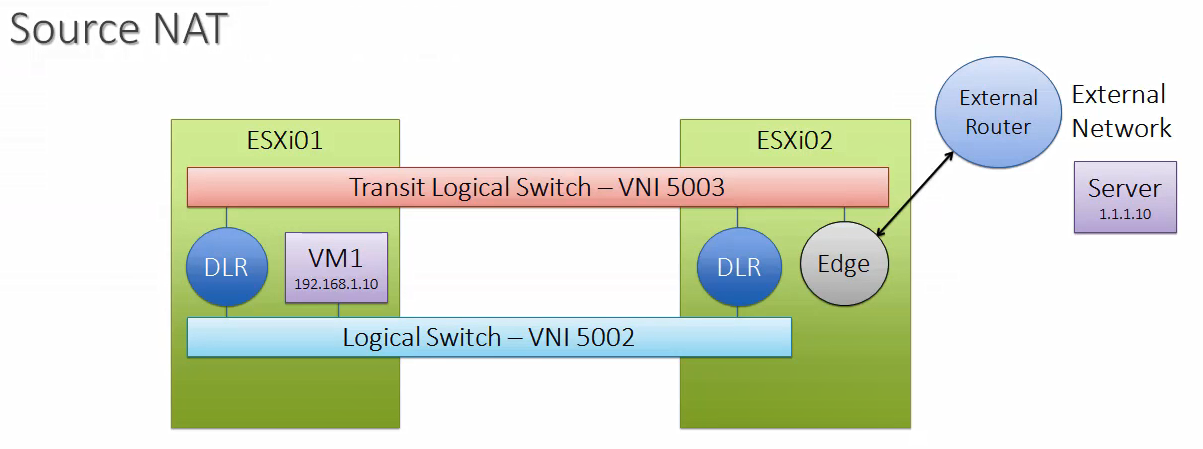
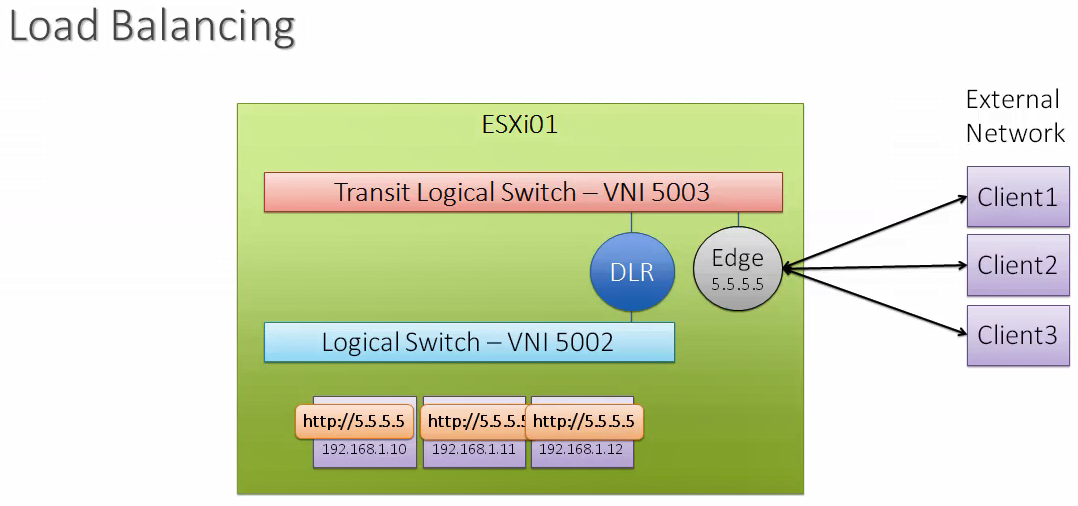
How it Works
NSX works by encapsulating the traffic that would normally be sent to the physical switches and routers inside an encapsulation protocol (like VXLAN, STT, and GRE). By doing this, the physical network hardware is compatible and doesn’t have to know anything about the network virtualization that is happening inside. It’s the NSX gateway that connects the virtual network to the physical network, but each hypervisor is running a special VMware NSX virtual switch and NSX controllers (which are virtual appliances) serve as the management plane, controlling it all.
Host Preparation
Host preparation is the process in which the NSX Manager installs NSX kernel modules on ESXi hosts that are members of vCenter clusters and builds the NSX control-plane and management-plane fabric. When a new host is added to this cluster, the required software is automatically installed on the newly added host. This kernel module enables below capabilities
- VXLAN
- Distributed Logical Router
- Distributed Firewall
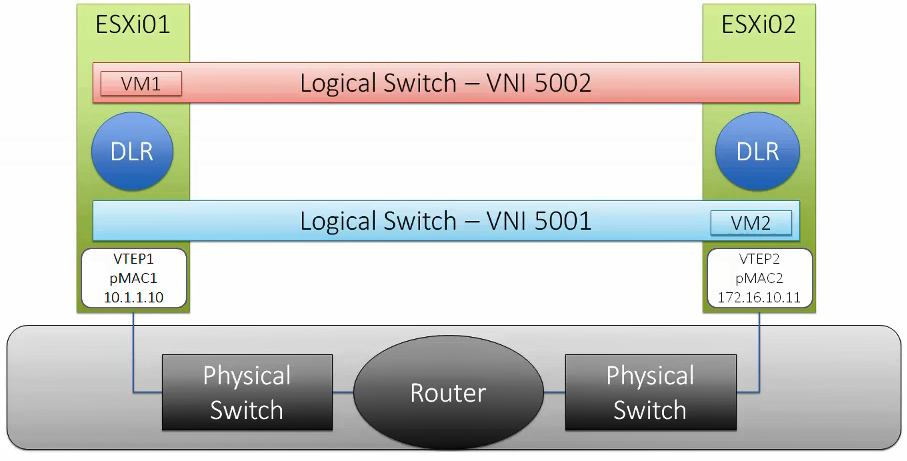
VXLAN
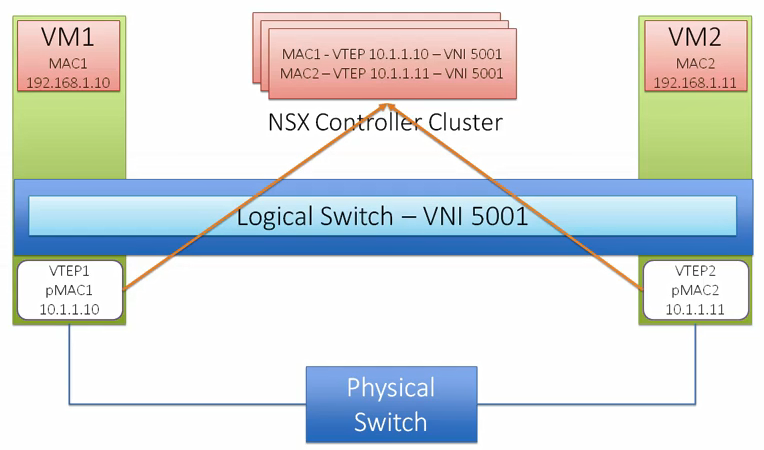
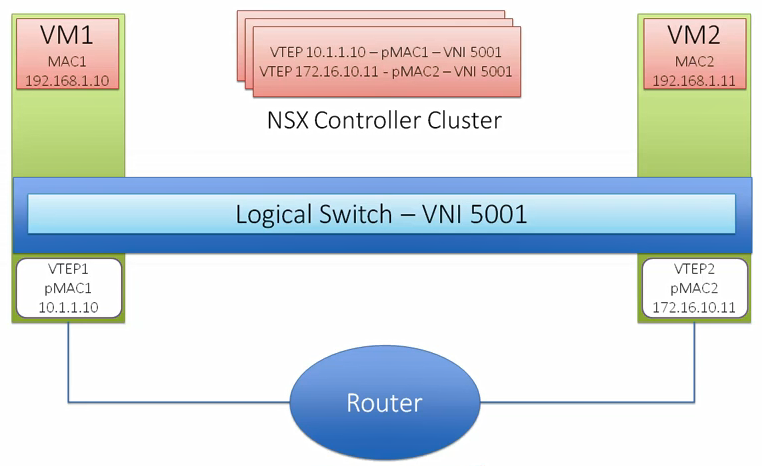
VXLAN is a tunneling protocol that encapsulates Layer 2 Ethernet frames in Layer 3 UDP packets, enabling you to create virtualized Layer 2 subnets, or segments, that span physical Layer 3 networks. Each Layer 2 subnet is uniquely identified by a VXLAN network identifier (VNI) that segments traffic. The entity that performs the encapsulation and decapsulation of packets is called a VXLAN tunnel endpoint (VTEP) and resides in hypervisor hosts.
- The MTU required for VXLAN encapsulated frames is 1600
- NSX implementation of VXLAN uses UDP port 8472
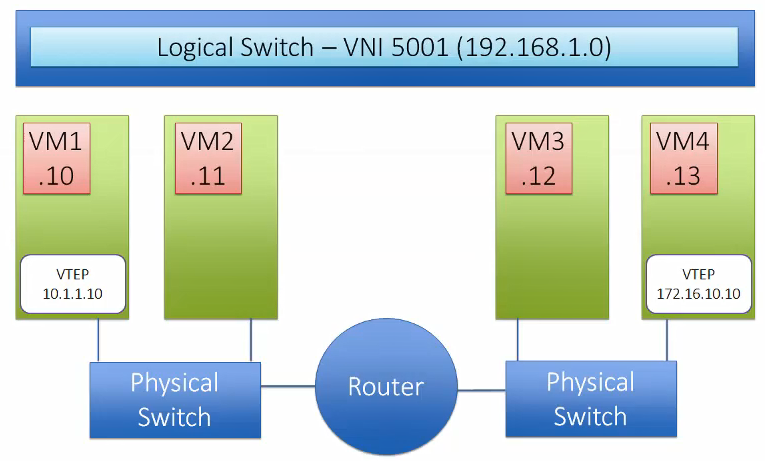
VTEP
Virtual Tunnel Endpoint (VTEP) are VMkernel ports on each host which is required for VXLAN. This encapsulates and decapsulates traffic with VXLAN headers. A VTEP has two logical interfaces, an uplink and a downlink. The uplink is responsible for receiving VXLAN frames and acts as a tunnel endpoint with an IP address used for routing VXLAN encapsulated frames. Below diagrams shows how the VM-to-VM communication happens in different scenarios.
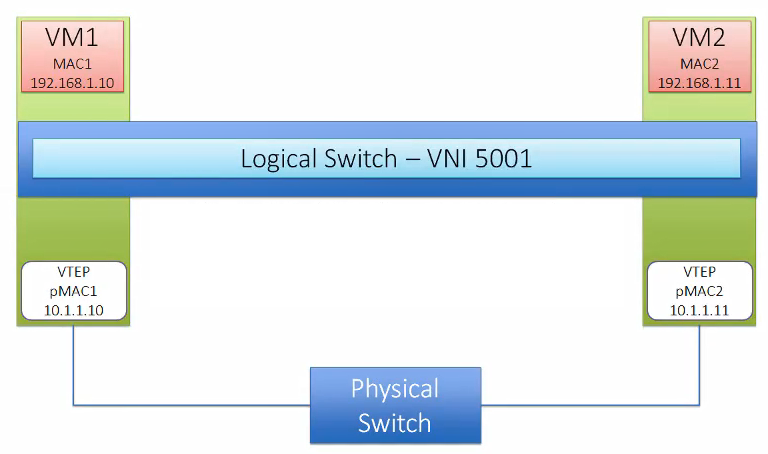
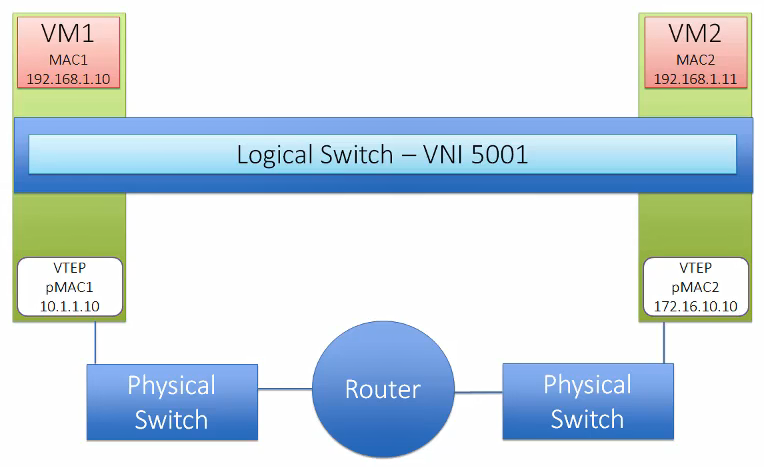
Logical Switch
NSX Logical switch is based on Kernel modules backed by vSphere distributed switch. This is identified using a pool of Virtual Network Identifier (VNIs). Logical switches provide VTEP functionality to support VXLAN and can span across multiple Distributed Virtual Switch.
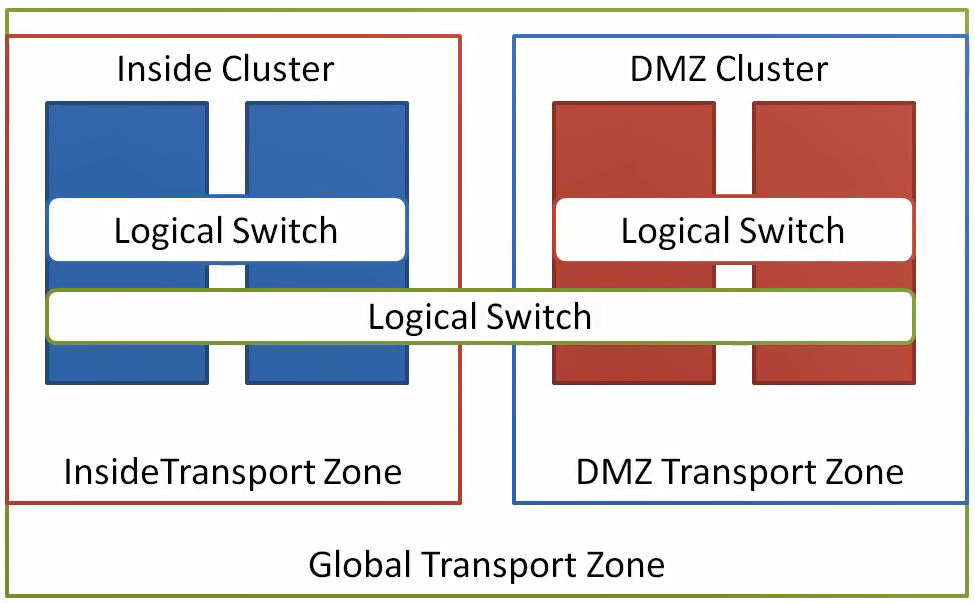
Transport Zones
A transport zone is a user defined scope for VXLAN networking traffic. The scope is defined by you as a set of clusters that will operate in this transport zone. You can define multiple transport zones, or just a single transport zone, it all depends on your environment.
- Identifies the scope of Logical Switch
- VMs in different transport zone cannot be on the same Layer 2 network
- Transport zones can be used to segment the NSX network
User World Agent (UWA)
This is an agent runs on ESXi host, which is used to communicate between the hosts. As VMs are connected to the network the UWA is used to inform the NSX controller and update the required tables. All these communications are SSL encrypted. User World Agent (UWA) runs as a daemon on all host called netcpa. UWA is not used to manage the distributed firewall. NSX Manager communicates with vsfwd daemon directly
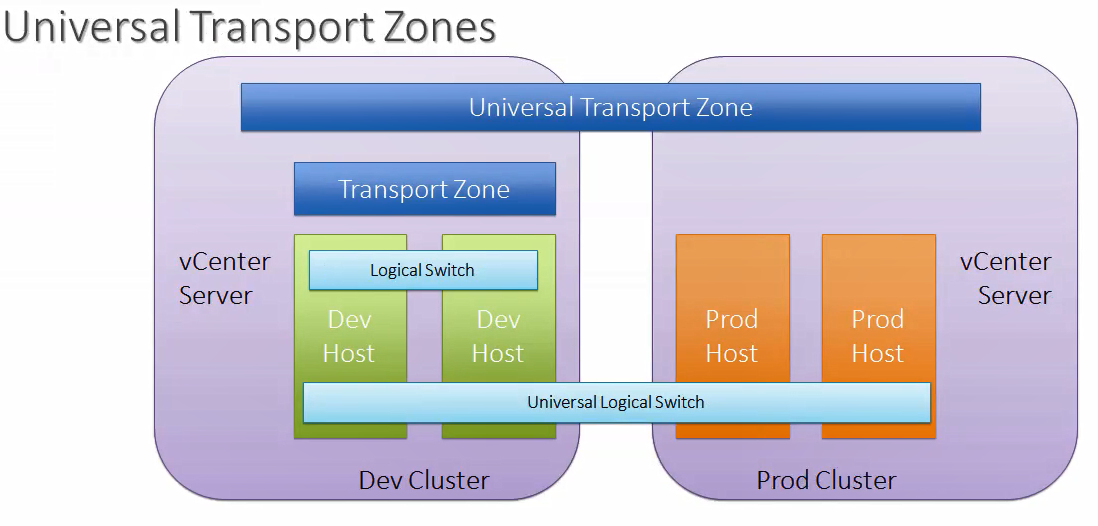
Cross-vCenter Support
NSX 6.2 or later version supports cross-vCenter NSX, means multiple NSX sites and vCenter servers can be linked together. Logical switches, Distributed Firewall rules and Distributed Logical Routers can span multiple vCenter inventories.
Features
VMware NSX is the network virtualization platform for the Software Defined Data Center (SDDC), which is a completely non-disruptive solution as it reproduces the entire networking infrastructure in software which includes L2-L7 network services. NSX allows virtual networks to connect to physical networks by maintaining fine-grained security as per virtual NIC. NSX has a wide range of features and below are some of them.
- Logical Switching
- Gateway Services
- Logical Routing
- Logical Firewall
- Extensibility
- Load Balancer
- Dynamic Host Configuration Protocol (DHCP)
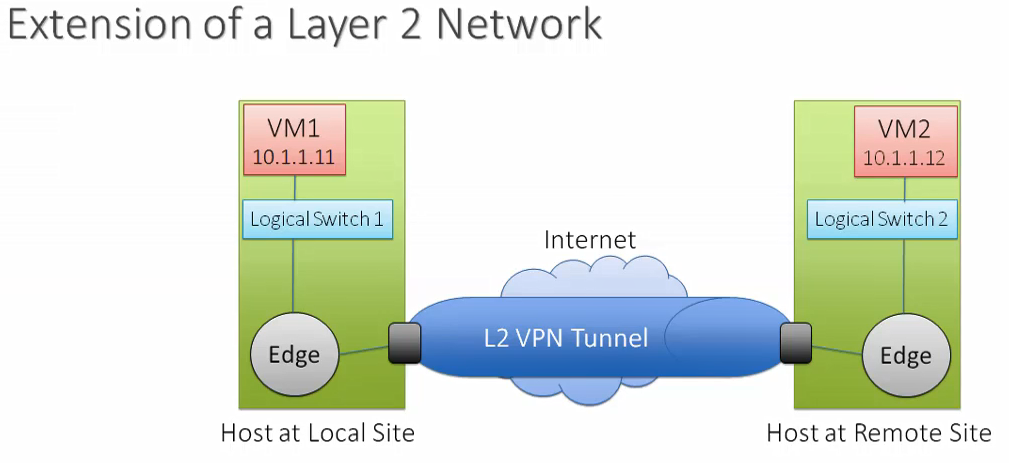
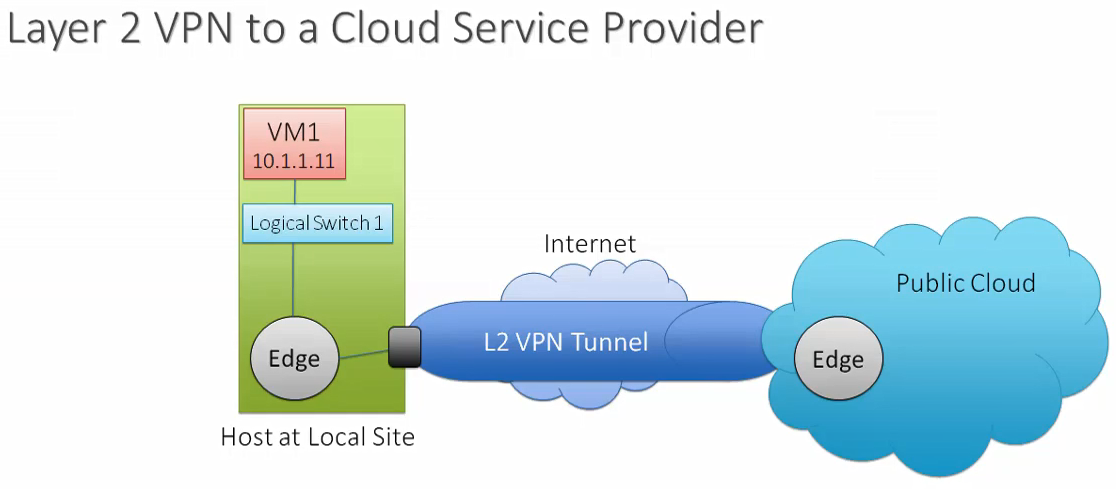
- Virtual Private Networks (VPN)
- Domain Name System Relay (DNS)
- Service Composer
- Data Security
- Trace Flow
- Flow Monitoring
- Activity Monitoring
Licensing
VMware NSX licensing is associated with the number of physical processors, A physical processor corresponds to a socket. The licensing model will be on per powered on VM basis for public cloud providers. There are two type of edition in VMware NSX
- VMware NSX for vSphere 6.x
- VMware NSX Data Center for vSphere 6.4.1+
Please use VMware KB for more details like editions and respective features.
Config Maximum / Interoperability Matrices
To check the configuration maximums and the features use the VMware Configuration Maximum URL
To check the compatibility between products, use the VMware Interoperability Matrices URL
To make this NSX series more understandable, i am splitting this in to multiple blogs
Part 2 – NSX Manager 6.4.x Installation & Configuration
Part 3 – How to Install Microsoft CA Signed Certificate In NSX Manager
Part 4 – VMware NSX 6.4.x Configuration
Part 5 – VMware NSX Logical Switching and DLR Configuration
Part 6 – VMware NSX Edge Configuration
Part 7 – How to Upgrade NSX Manager
Thanks,
If you have any comments, please drop me a line.
I hope this article was informative, and don’t forget to buy me a coffee if you found this worth reading.



Leave a Reply